I recently received a phishing email to analyze, let’s see how to unbox all the components and identify them using Malcat.
We can notice how good is this phishing attempt :
– the sender was known by the recipient
– the mail was written in correct french (quite unusual)
– the mail contains and old discussion from 2021 between the (true) sender and the recipient : this technique is called “thread hijacking“
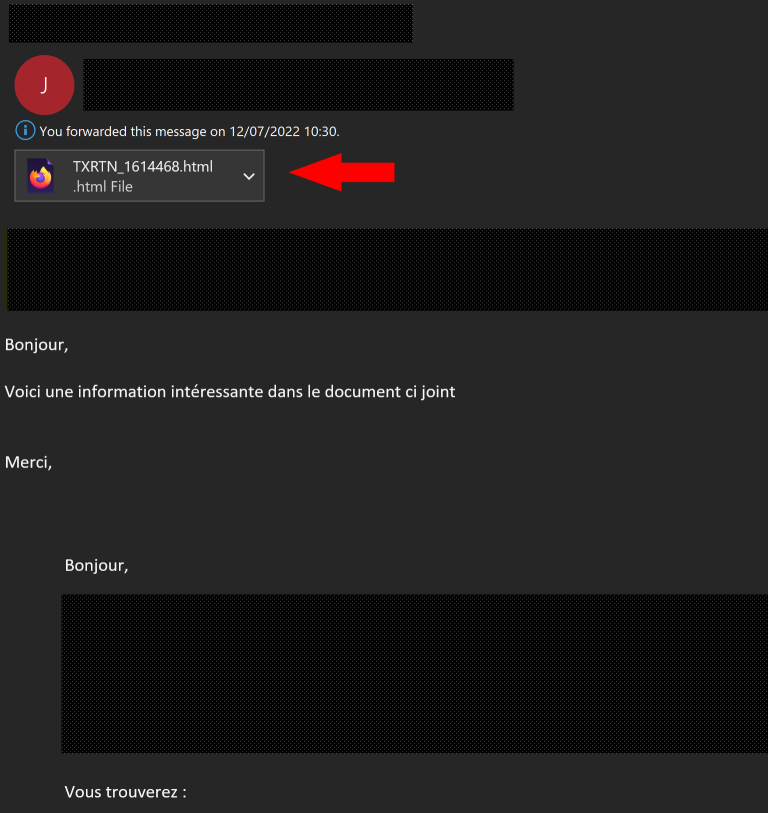
The email contains a HTML file as attachment, which once opened shows an Adobe logo, a password (“abc321“) and prompt the user to save the file "TXRTN_1614468.zip" locally :
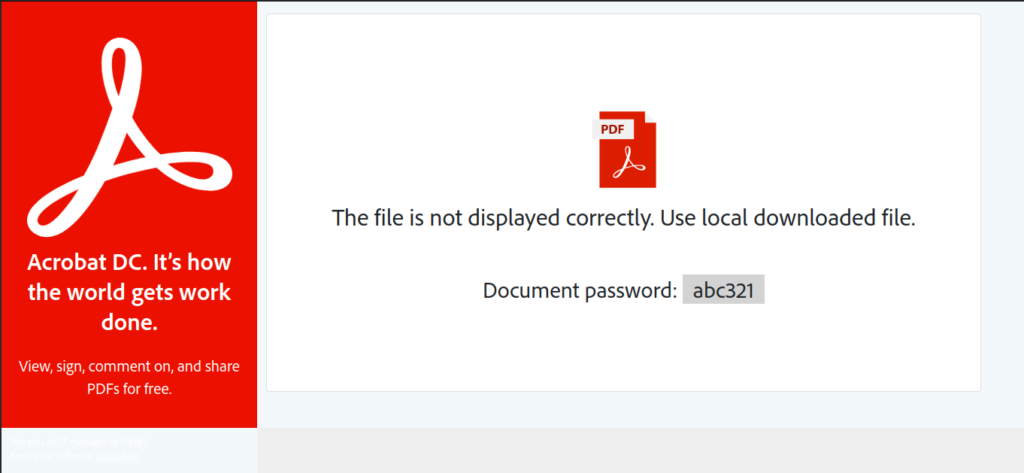
The technique to embed a file directly in the HTML code is called HTML Smuggling.
The password protected ZIP file contains an ISO file :
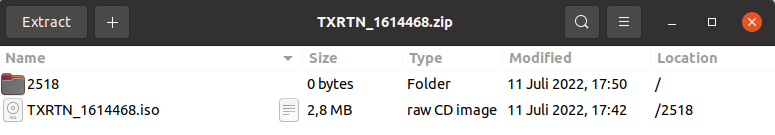
Mounting the ISO in linux only shows 1 LNK file (even with “show hidden file” option).
Mounting the ISO in Windows shows 4 files (3/4 are hidden).
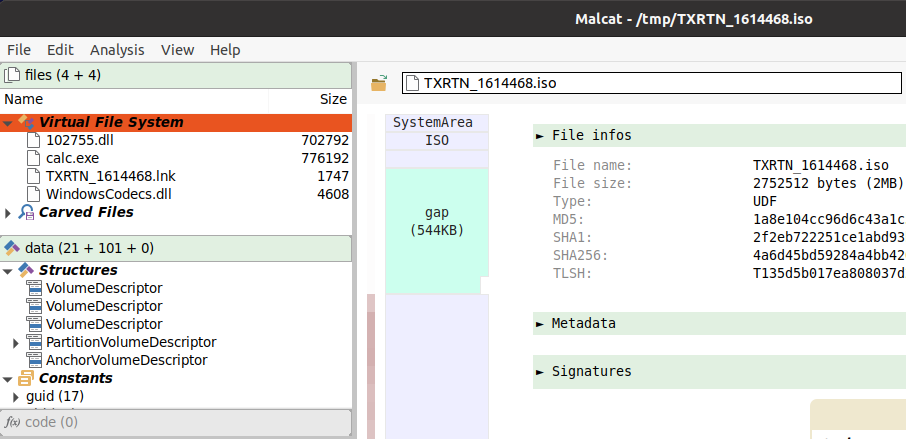
I like also opening files with Malcat, which recognizes the ISO format and shows the content :
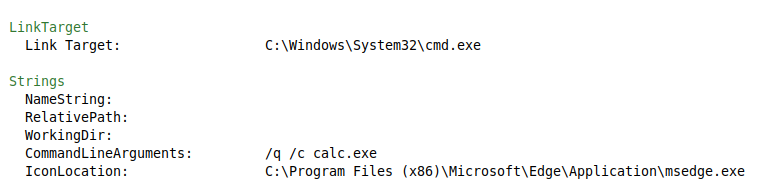
Still using Malcat, we can open the LNK file (which is supposed to be clicked by the targeted user) and see that it runs “C:\Windows\System32\cmd.exe” with “/q /c calc.exe” as parameter, and uses “C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe” as icon :
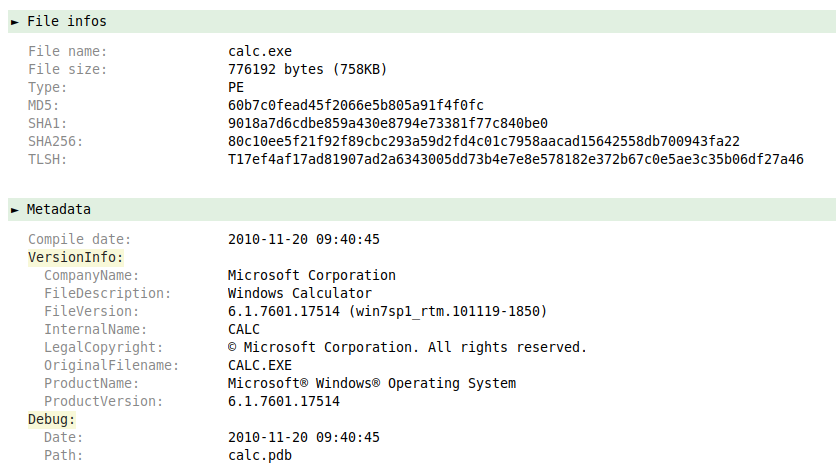
Again in Malcat, we can now open the “calc.exe” and see that it’s a Microsoft binary from Win7 RTM :
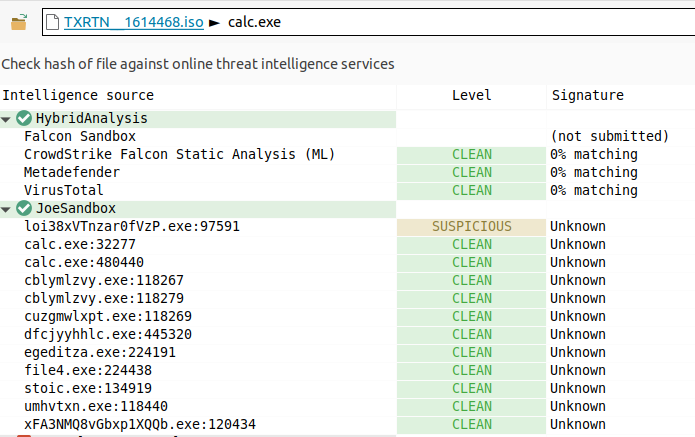
calc.exe“Using the “threat intelligence” tab we can confirm it’s clean :
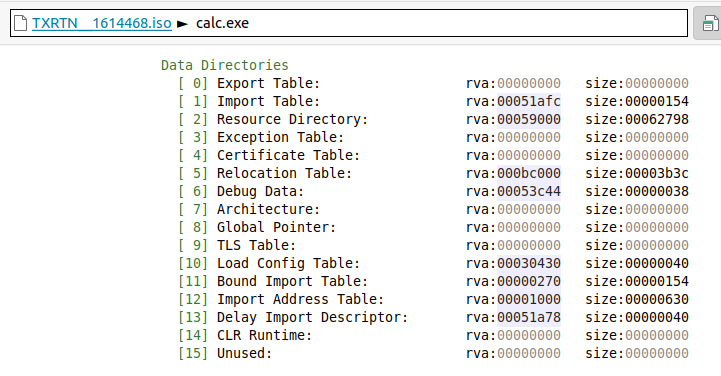
calc.exe“If we look at the “summary” tab, we see that beside having a regular “[1] Import Table” , the PE also has a “[13] Delay Import Descriptor" which are the DLLs that are loaded later because their functions are not critical for the program :
calc.exe“The only “Delayed Import” is “WindowsCodecs.dll” :
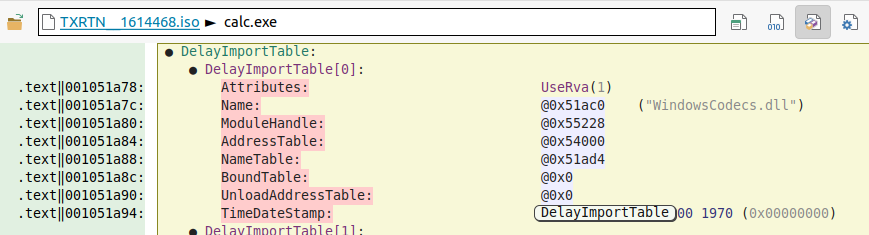
Since we have a copy of this “WindowsCodecs.dll” on the ISO file in the same folder as “calc.exe“, it’s the one that will be loaded instead of the official one located in “C:\Windows\SysWOW64".
This technique is called “T1574.001 : DLL Search Order Hijacking” (MITRE)
Using the “threat intelligence” tab of Malcat, we already see that something suspicious is ongoing :
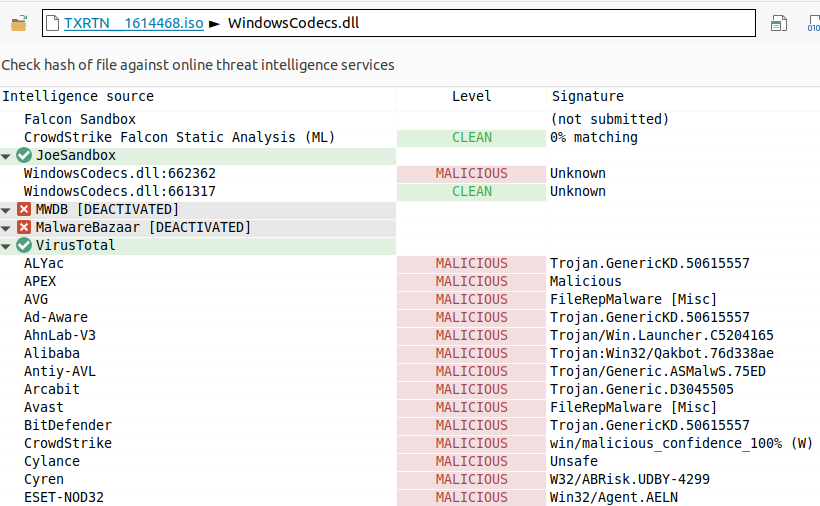
WindowsCodecs.dll“We use the “symbols list” tab to jump to its EntryPoint and the “decompiler view” tab to view it in pseudo code. It’s easy enough to understand that when the “WindowsCodecs.dll” is loaded, it checks whether we are on 32bits or 64bits system, and runs “<SystemRoot>\regsvr32.exe 102755.dll“
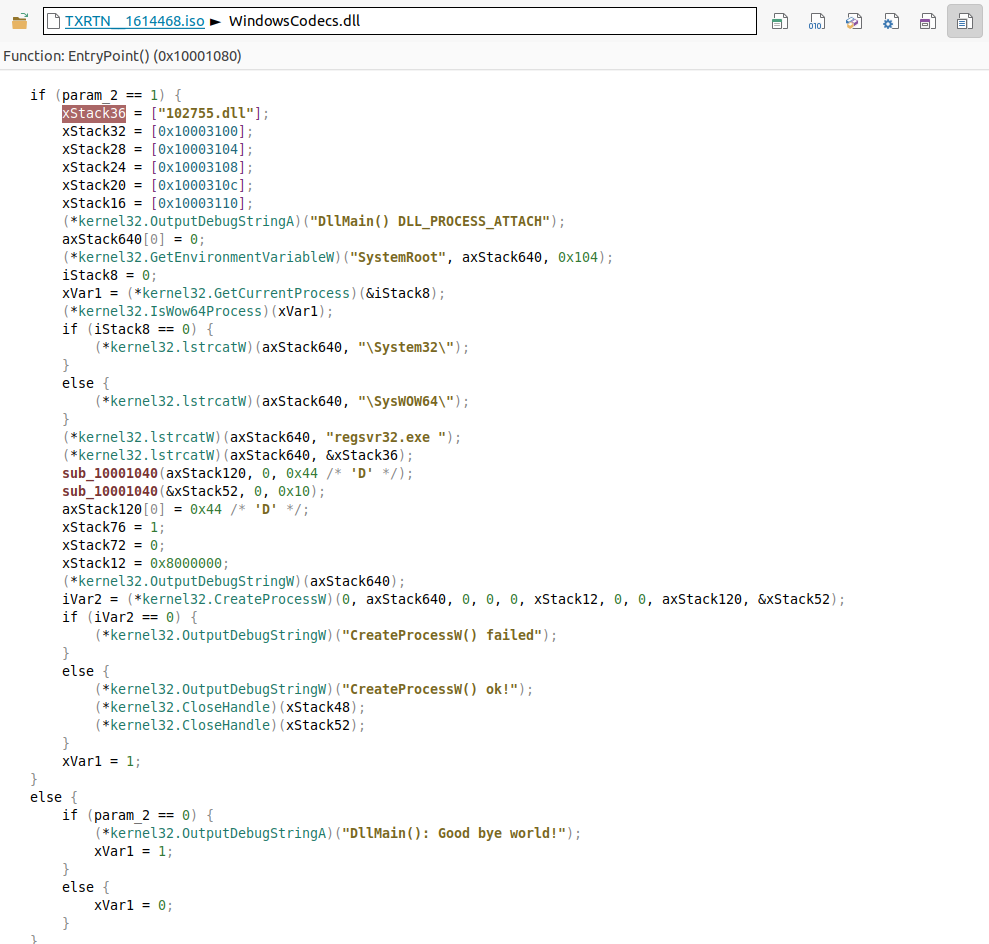
WindowsCodecs.dll“As we have a copy of “102755.dll” on the ISO file, let’s take a look at it.
The “Anomalies” section in the “summary” tab already shows the usual suspect indicators (DllNoExportTable, PossibleDownloaderApiDynamicImport) :
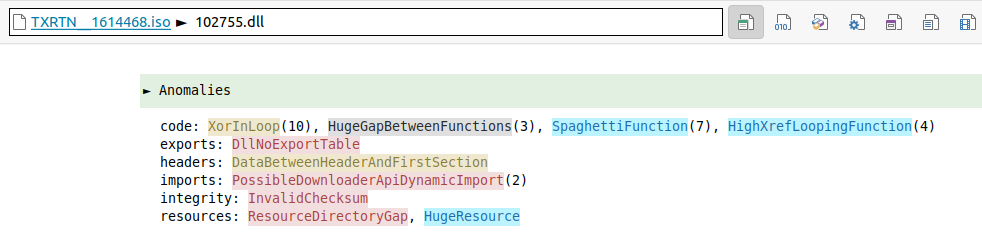
102755.dll“We now have the full chain of actions for the target to be infected :
HTML -> ZIP -> ISO -> LNK -> EXE -> DLL -> DLL
Since we still don’t really know what is the last DLL we can check the “threat intelligence” tab, but surprisingly, this DLL is reported as NOT FOUND :
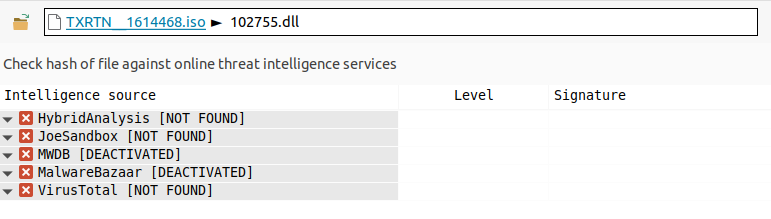
102755.dll“If this malicious file is not known by any of the Malware databases, it’s because its hash (MD5 or SHA256) has never been seen and is unique : each variant of this DLL has a different hash.
This technique is called hashbusting and is easy for attackers to implement just by modifying a few useless bytes of the file before sending it to their victims.
Another approach to identify “known” malicious files is using imphash values. The imphash is calculated using the imported libraries/functions of the PE and their order. This calculation has been added to the pefile python library (“python -m pip install pefile“). 3 lines of python are enough to calculate it :
>> import pefile
>> pe = pefile.PE("102755.dll")
>> print(pe.get_imphash())
05ed4a07fc9a6a7112c8cd9c50f474b3
MalwareBazaar is kind enough to let us search by imphash values and we see that this “102755.dll” is just another Quakbot Malware variant :
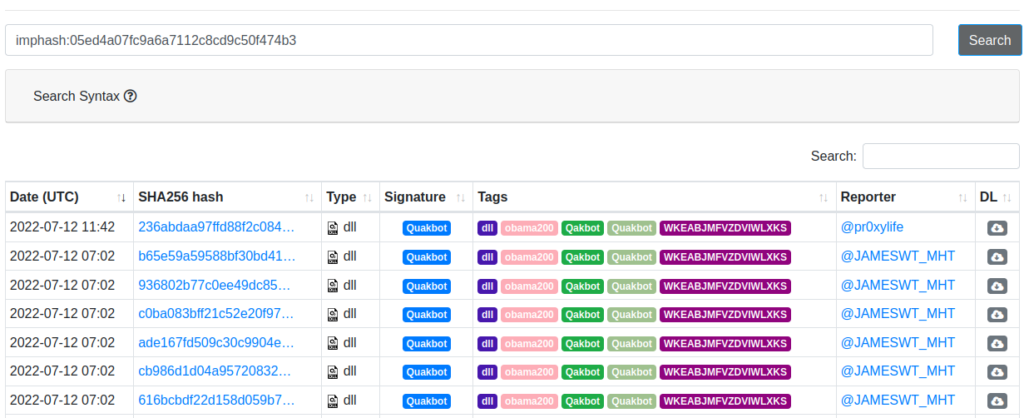
There are some ways to defeat imphash but this time, it worked !