SANS FOR610 Training
The full name of the FOR610 training from SANS is “Reverse-Engineering Malware: Malware Analysis Tools and Techniques”. The goal is to learn how to efficiently analyze malwares in various forms (mainly Windows and Script files) depending on what is the purpose of the analysis : to understand how a security incident started, to provide some IOC to a detection team/system, to propose some eradication methods…
The course is 5 days long, accessible even if you know nothing about assembly, but it helps a lot if you already have an idea of what it is. The 6th day is not mandatory, but is a very fun CTF, allowing students to practice what they learned during the course. One week before the training, students are able to download the materials (watermarked PDF) and the LAB images (you need a powerful enough PC to run 2 VMs simultaneously).
The course is available remotely, but for a more immersive experience, I think going on-site is really better. I attended this course in November 2022 during SANS Paris Event and I liked a lot meeting new people from the Cyber Security world, and discussing with our instructor Jim Clausing.

Day 1 : Malware Analysis Fundamentals
After a warm welcome from the SANS Team, students are invited to join their classroom where SANS books and gifts are offered to them. Every student should have prepared his LAB environment before the training, but in case of any issue, we had 30 minutes on the first morning to solve them (setup REMnux + Windows machine + network settings). Once everything was working, the instructor introduced himself and the course started with the fundamentals : static analysis, behavioral analysis and ended with a bit of dynamic analysis. It was a fun day during which we learned how to use the LAB and discovered a lot of different tools.
Day 2 : Reversing Malicious Code
The second day was fully dedicated to assembly language : instructions, registers, functions prologue/epilogue, stack, memory, control-flow, and a bit of Win32 API calls while practicing reverse engineering on some samples provided in the LAB. It went fast because there was a lot of things to see, especially for people having no clue about what is assembly. At the end of the day, a few of us were a bit lost, but after reading the PDF a second time, they were back on track and ready for the next day !
Day 3 : Analyzing Malicious Documents
This day was dedicated to the analysis of malicious documents : PDF, Microsoft Office (Word/Excel) with their VBA scripts, and RTF with embedded shellcode. We practiced on a lot of different documents, and with a lot of different tools again. Since phishing / malicious documents is the #1 initial vector of compromise, it’s important to understand what you can do with a simple document.
Day 4 : In-depth Malware Analysis
Now the basics were covered, we dug into more advanced things : obfuscated JS and VBS, unpacking malware following different approaches (time to fire x64dbg !), a very long/complex malware case with multiple technologies involved, and eventually some examples of code injection and API hooking.
Day 5 : Examining Self-Defending Malware
In the wild, most of malwares are self-defending, so we had to understand the various methods of anti-debugging and data obfuscation. We had samples with Process Hollowing capabilities, a very aggressive sample trying to detect tons of stuff. We also saw 2 very important concepts : SEH (Structured Exception Handling) and TLS callbacks : a must ! Last part of the day was focused on how to unpack malware by anticipating what they’re going to do (which APIs are going to be used), which gives a more or less generic approach to it.
Day 6 : Capture The Flag
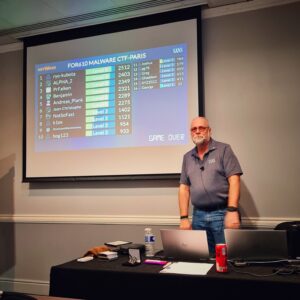
This day is optional, but I highly recommend to participate, it gives opportunity to practice on what we learned during the week (6th day is a Saturday). The instructor was still present in the classroom, but stayed quiet, every challenge was accessible though a local website and their difficulty was progressive (you need to solve the first challenges to unlock the next ones). The score was given live on the projector, it was very exciting and motivating. Depending on the number of students there are 1 or 2 (or maybe 3) medals (called coins) you can win. In my case, we were 16 students for 2 coins, I finished at 3rd place so I didn’t have the chance to win a coin 😥.
GREM Certification
After following the FOR610 training, the next logical step is to attempt the GIAC Reverse Engineering Malware Certification (GREM).
If you purchased a bundle, one week after the end of the training you’ll get access to 2 practice exams + 1 exam attempt via your SANS Dashboard. You’ll have 4 months before expiration of the exam attempt voucher. In my case, I’ve been really lazy and took the exam on the last week of availability (10th of April) and remotely as there was no exam center in Belgium.
The exam is made of 66 questions (55 multiple choices + 11 Cyber Live (which are small LAB exercises in a VM)). Duration is 3 hours and you need 73% to pass it.
To prepare the certification, it’s advised to create an index, but since there is already one at the end of book #5 and that you can find some good resources online (HERE and THERE), I decided not to.
First I read the 5 books completely (without doing the LABS), and highlighted all the topics I was not comfortable with or that were looking important (it took me 3-4 hours per book). I also had a copy of Mastering Malware Analysis – Second Edition from Amr Thabet and Alexey Kleymenov which helped me a lot !
Next, I choose to put all my highlighted topics in a OneNote (then in a Word document eventually) to help me to memorize and to understand them. For every topic, I wrote a brief explanation and the page reference in the official SANS PDF (in case I would need it during the exam).
When I did this for the 5 books, I decided to take one of the practice exam to see what kind of questions it will be and how far I was from being “ready”. I scored 97% in 1h40. Time didn’t seem to be a problem for me.
The next 2 days, I was feeling confident, so I took some rest and read a few topics which I didn’t fully understand.
I took the second practice exam and I scored again 97%, a lot of questions were similar to the first one ! It seems the pool of questions for the practice exams is not that big.
The day of the exam, I received an e-mail with a link to open in Guardian (the custom browser from ProctorU you need to install prior to the exam). Then I needed to install a LogMeIn application to get in touch with my remote proctor. The guy was really nice and checked a few things on my computer (no VNC installed, no keylogger), in my environment (windows, doors, desk, mousepad…), and wished me good luck.
During the exam, you can skip some questions, but you’ll have to answer them before being able to take a break. Also, when you answered a question, you can’t come back to it (meaning you cannot check something in the LAB environment then come back to the theoretical questions…). I didn’t have any question in common with the practice exams, I think the pool of question is completely different, but they are very similar (same difficulty).
I passed with 97% again in approximately 2h10 (I really took my time on some question as I knew I would have some time left).

The next days, I received some emails from SANS to congratulate me and to claim my badges on Credly so that I could proudly share them on LinkedIn. I was also invited to the GIAC Advisory Board since my score was >90% (board enrollment is optional).


Hope this post will help or give some good hints if you plan to follow the FOR610 training and/or the GIAC Reverse Engineering Malware Certification (GREM) ! Don’t hesitate to leave a comment or contact me if you have any question (but don’t ask me to share the SANS PDF, I won’t 😑)