This is a small write-up of the “Sniffed Traffic” challenge from SEECTF 2022 (Forensics Category).
Description :
Author: Enyei
We inspected our logs and found someone downloading a file from a machine within the same network.
Can you help find out what the contents of the file are?
For beginners: https://www.javatpoint.com/wireshark
MD5: 71cd3bdbecece8d7919b586959f2d3b7
Solution :
Once the capture file opened with Wireshark, we can start filtering the packets because we know from the description that the source and the destination IP are on the local network :ip.src == 192.168.0.0/16 and ip.dst == 192.168.0.0/16
We now have “only” 158 packets to inspect :
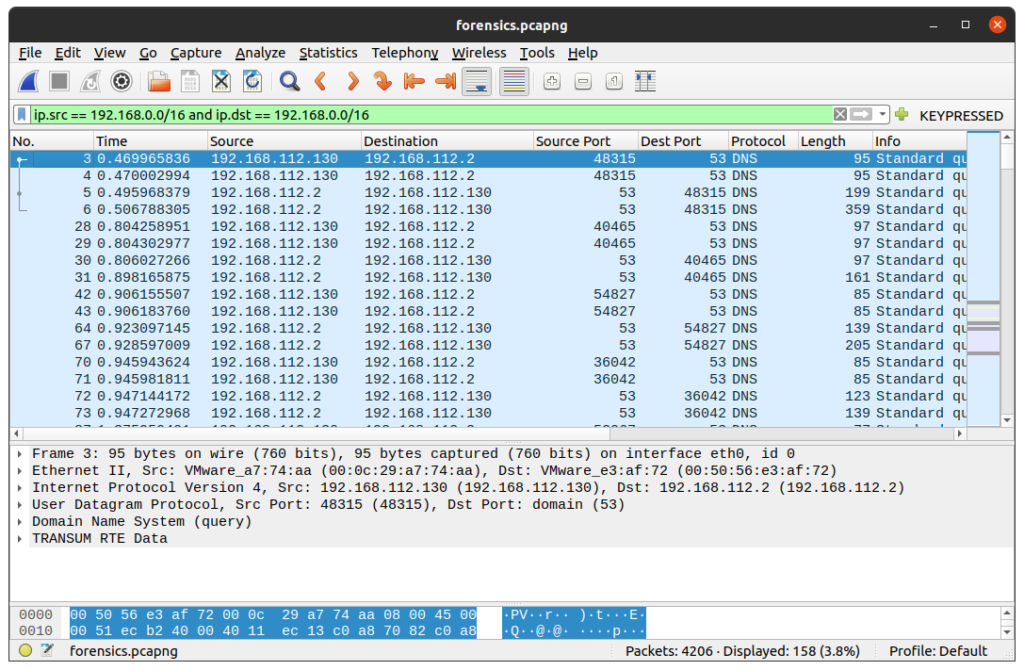
Let’s scroll a but through the packets and we’ll find that packet 3838 is a HTTP GET request, replied by packet 3844 :
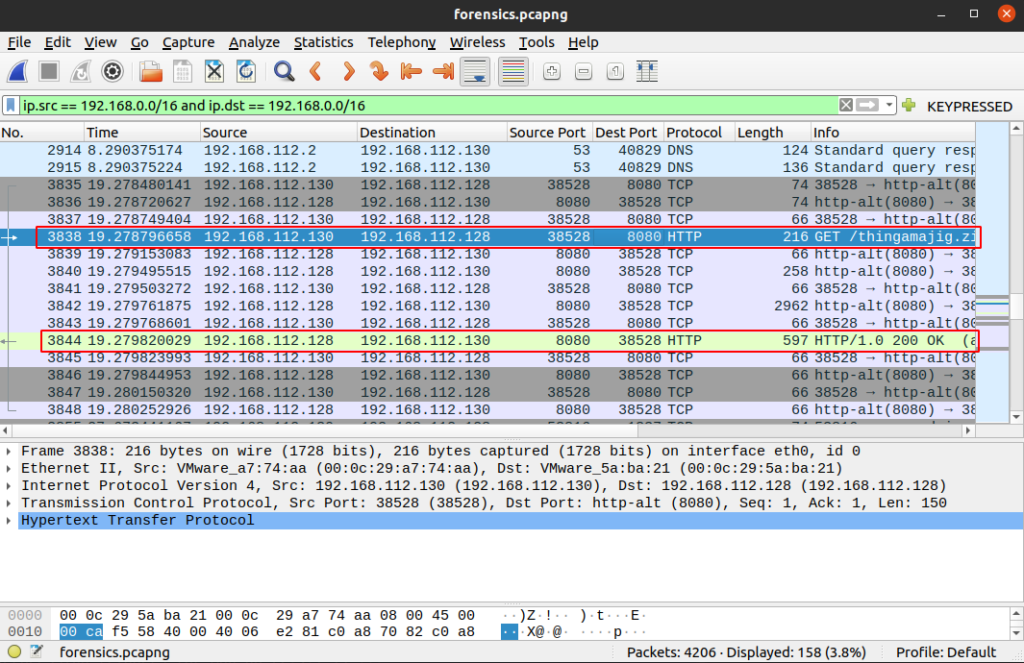
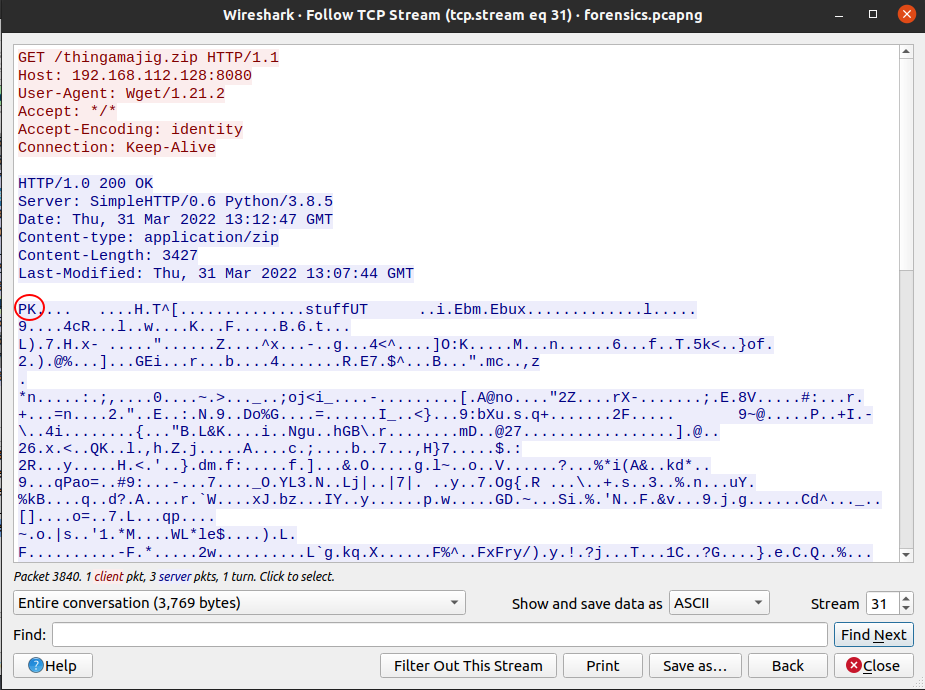
Select packet 3838 and go to “Analyze” -> “Follow” -> “TCP Stream” (or Ctrl+Alt+Shit+t) to view the conversation between the 2 hosts. We notice that the answer from the HTTP server (192.168.112.128) is a ZIP file (“PK” in the header).
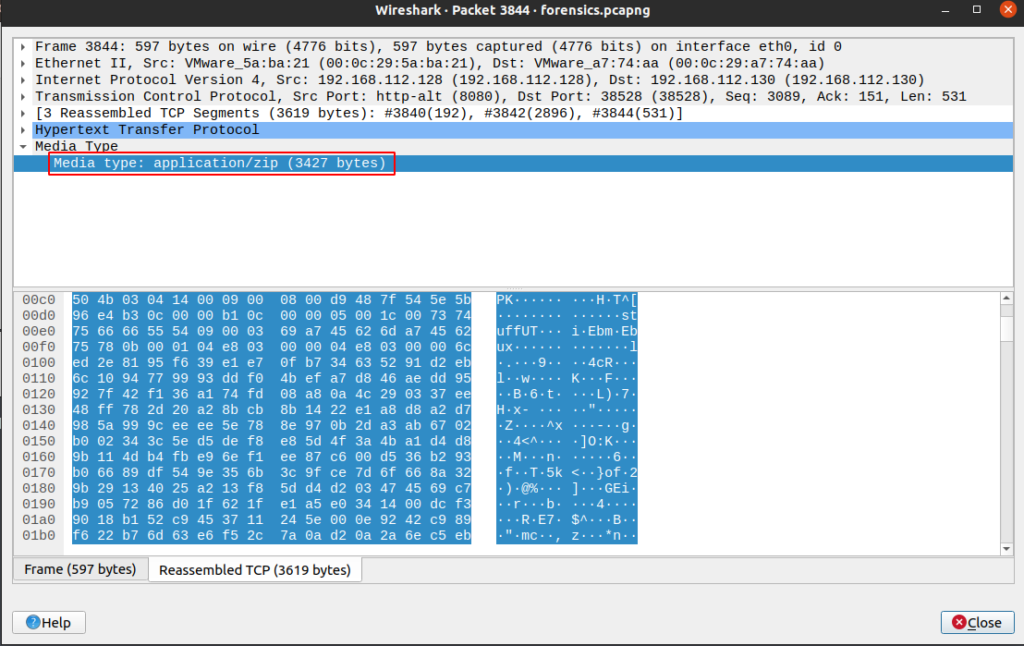
To save the content of the server reply, double click on the packet 3844 in the main window of Wireshark, right click on the “Media type: application/zip (3427 bytes)” line and “Copy” -> “… as raw binary”
Open any hex editor (I use Okteta) and paste the content of the file into a new file, then save it as “thingamajig.zip” (it’s the original name of the file).
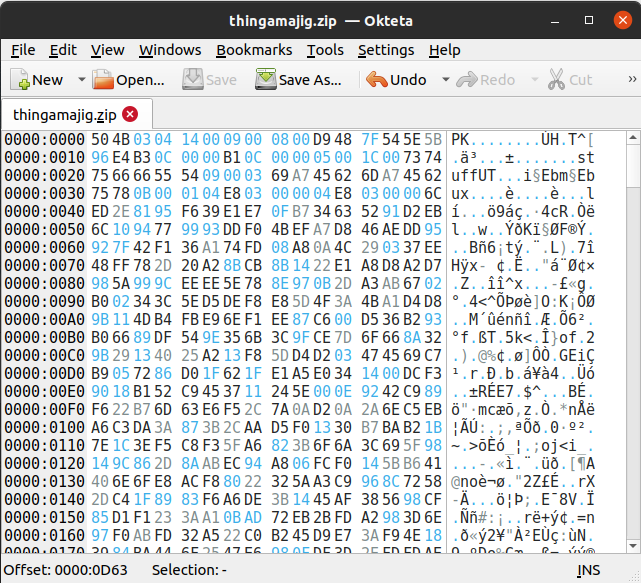
thingamajig.zipNow if we try to open “thingamajig.zip“, we notice it contains 1 file called “stuff” but the ZIP file is password protected.
To find the password, we need to continue inspecting the capture file in Wireshark. In the previously opened TCP conversation window, we switch to the conversation #32 and discover a clear-text discussion containing the password of the ZIP file (49949ec89a41ed9bdd18c4ce74f37ae4) :
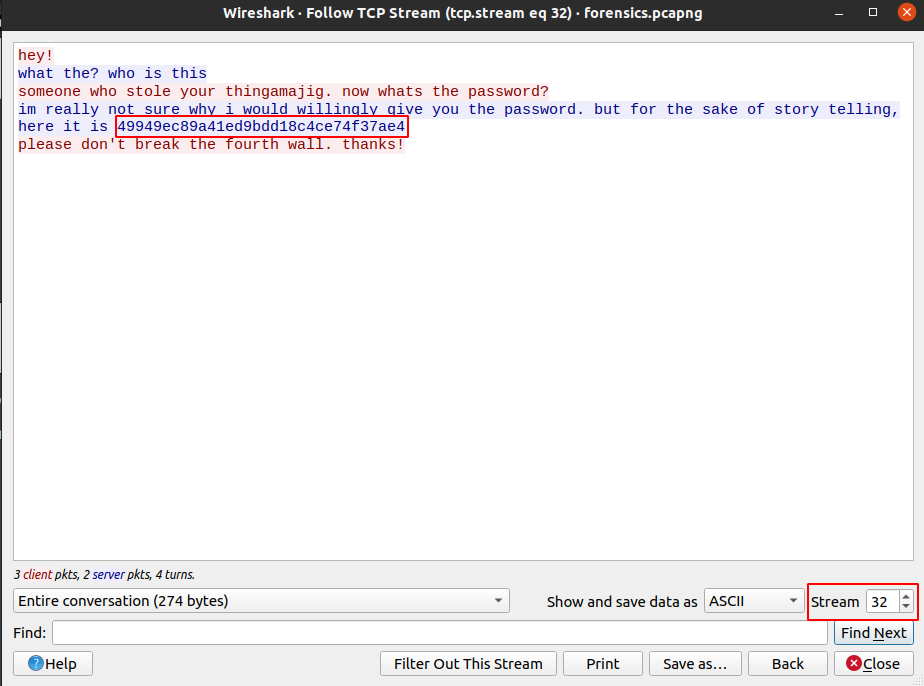
We can now extract the “stuff” file from “thingamajig.zip“. We can check it with the file command, but it’s unknown file type. Next we can check it with the foremost command to see if it contains known file types anywhere in the file. We notice that a small ZIP file is detected :
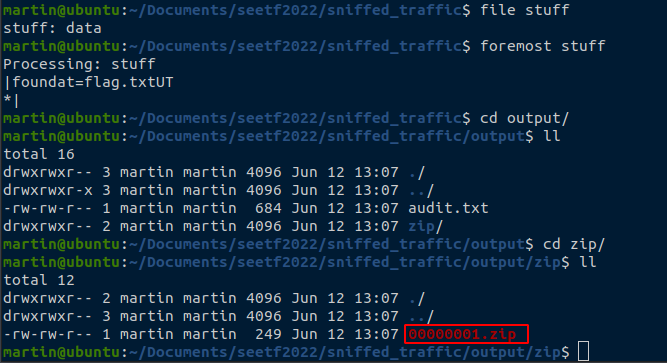
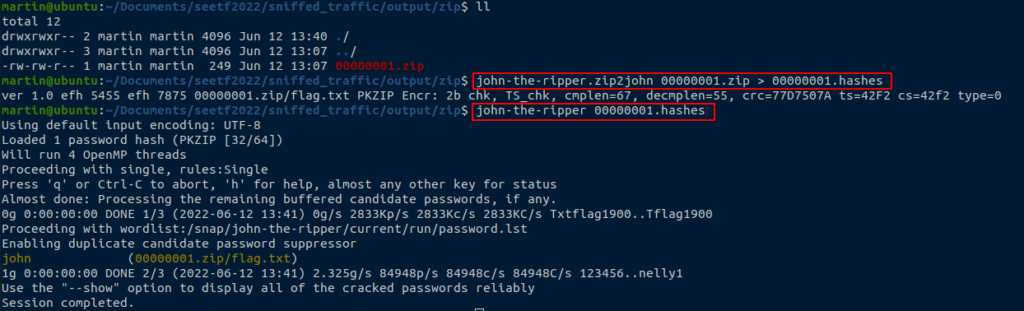
stuff with foremostTo crack the password of this ZIP, we’ll use John The Ripper (install with sudo snap install john-the-ripper if you don’t have it).
First create the hash file with : john-the-ripper.zip2john 00000001.zip > 00000001.hashes
Then brute-force the hash with : john-the-ripper 00000001.hashes
After a few seconds the password of the zip file appears : “john“
johnWe can now extract “flag.txt” and get the flag :
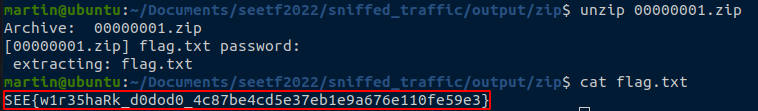
The flag we are looking for is then : SEE{w1r35haRk_d0dod0_4c87be4cd5e37eb1e9a676e110fe59e3}