This is a small write-up of the “Torrent Analyze” challenge from picoCTF 2022 (Forensics Category). The challenge is now available in picoGym here !
Description :
SOS, someone is torrenting on our network. One of your colleagues has been using torrent to download some files on the company’s network. Can you identify the file(s) that were downloaded? The file name will be the flag, like picoCTF{filename}
Hint 1 : Download and open the file with a packet analyzer like Wireshark.
Hint 2 : You may want to enable BitTorrent protocol (BT-DHT, etc.) on Wireshark. Analyze -> Enabled Protocols
Hint 3 : Try to understand peers, leechers and seeds. Article
Hint 4 : The file name ends with .iso
Solution :
As explained in the hints : download the capture file (.pcap) and open it with Wireshark, enable BitTorrent related protocols.
First, use filters to only display bt-dht traffic :
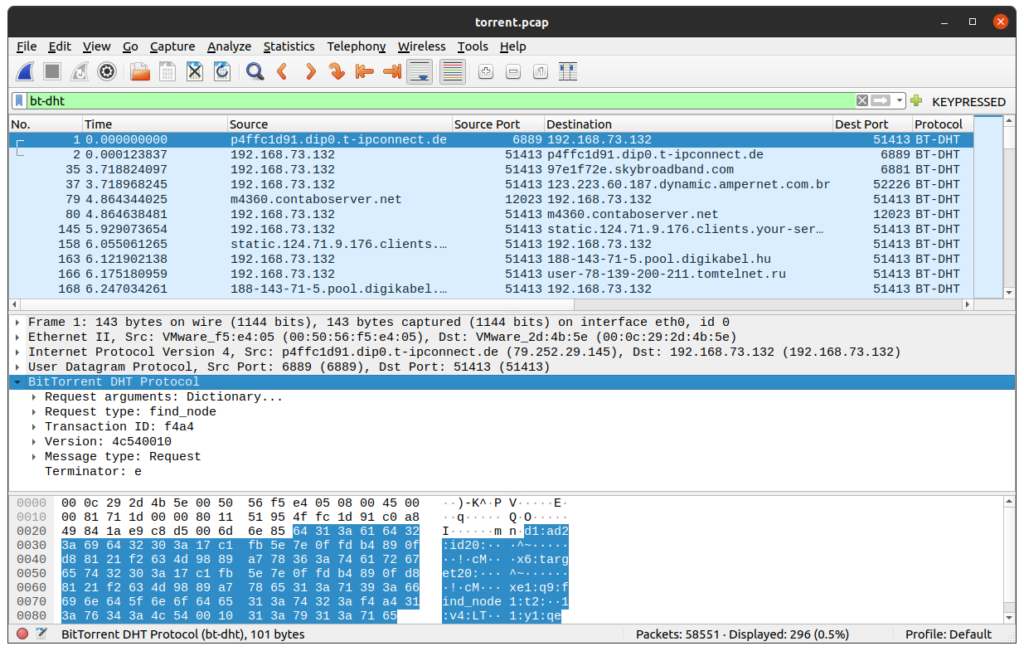
bt-dhtWe see now that the local IP address from which we are looking for more details is 192.168.73.132, let’s adjust the filters :
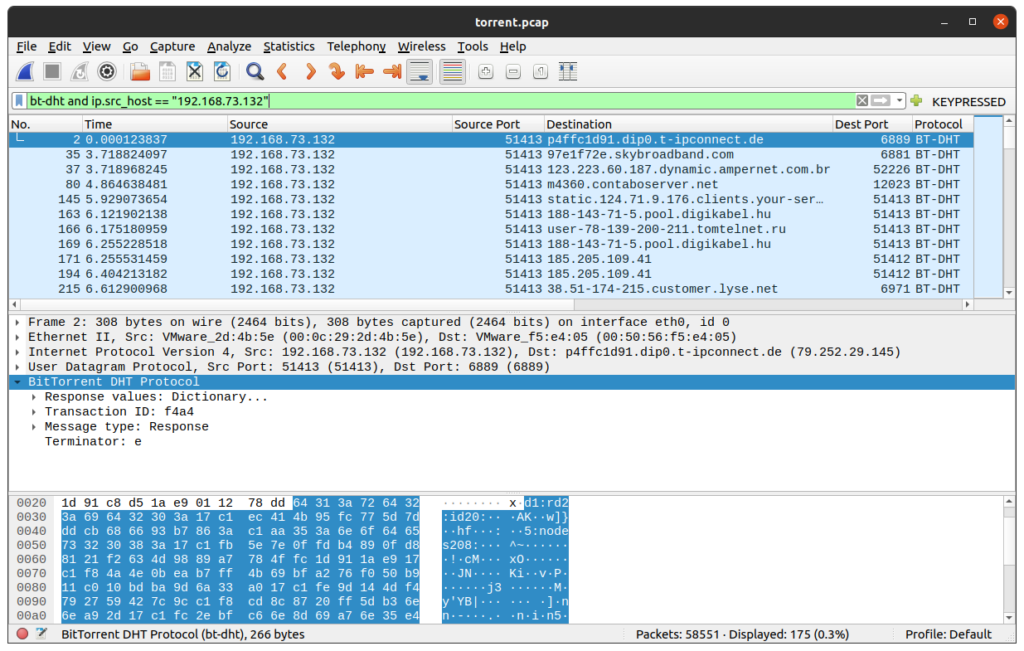
bt-dht and ip.src_host == "192.168.73.132"Navigate through the packets until you find one packet where “Message type: Request” and “Request type: get_peers“. The first packet of this type is the packet #51080
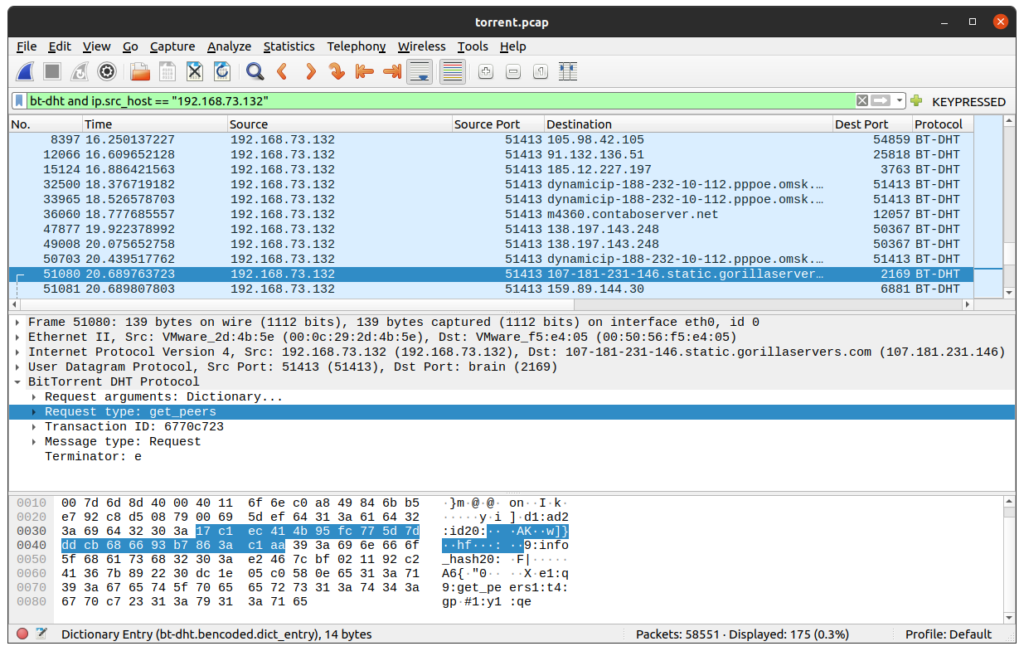
Unfold the “Request arguments” of the middle panel to find the info_hash value e2467cbf021192c241367b892230dc1e05c0580e
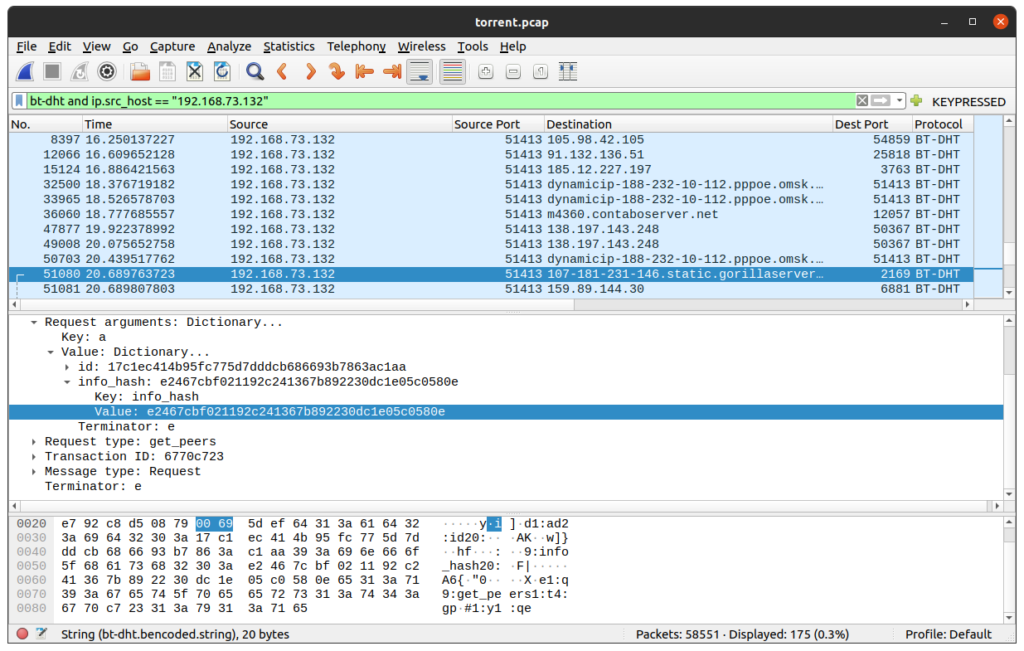
info_hash valueRight click on the value -> Copy -> Value, and search it in Google :
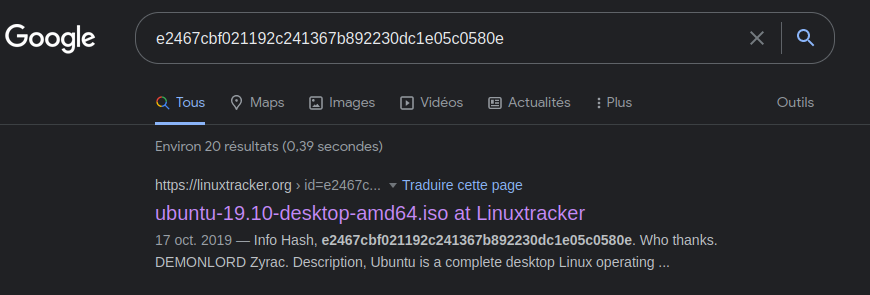
e2467cbf021192c241367b892230dc1e05c0580eThe flag we are looking for is then : picoCTF{ubuntu-19.10-desktop-amd64.iso}